What is AWS IAM?
AWS provides many services to its users. One of them is AWS IAM. This article will guide you on how to manage policies and permissions using AWS IAM.
AWS Identity and Access Management (IAM) enables you to handle AWS services and resources securely with a command line or without. Using the AWS IAM, you can create and manage AWS users, groups, policies, and roles. You can also use permissions to allow and deny their access to specific AWS resources and services.
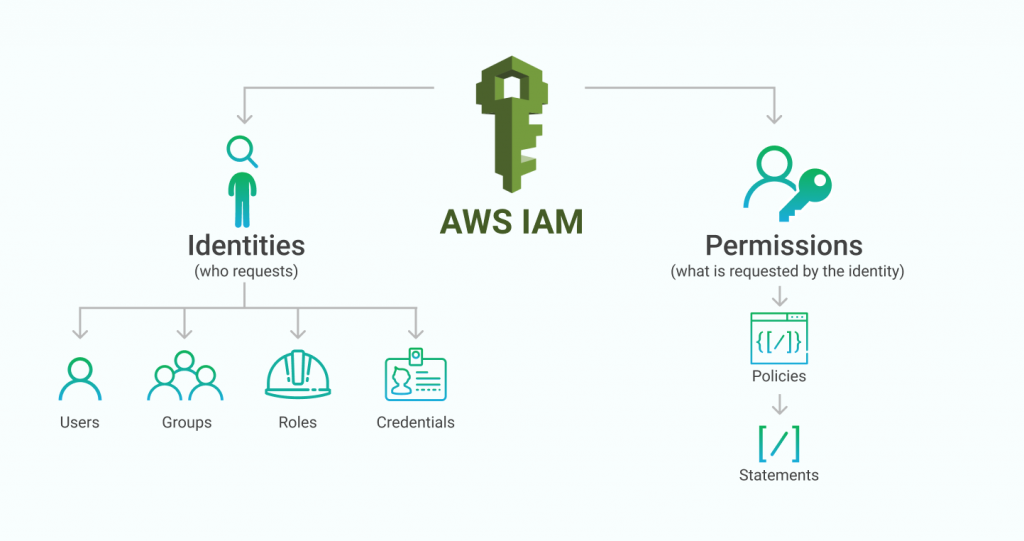
IAM Key Features
Four features of IAM are as follows;
- Granular control
- Multi-factor authentication (MFA)
- Temporary credentials
- Free to use
1:Granular control
IAM user is used for specific AWS services and resources using IAM policy/permissions. For example, terminating EC2 instances, reading an Amazon S3 bucket’s contents, managing the AWS Lambda applications, etc.
2:Multi-factor authentication (MFA)
You can add two-factor authentication to your account and users separately for extra security. With MFA, you or your users provide not only a password or access key & secret key to work with your account but also provides code from a specially configured device.
3:Temporary credentials
To define access permissions directly to users and user groups, IAM lets you create roles & policies. Roles allow you to define a set of permissions. In addition, you can increase your security by providing temporary access to your services.
4:Free to use
AWS Identity and Access Management (IAM) is a service of your AWS console account. AWS doesn’t take an additional charge for IAM service. You will pay only for the other AWS services through using the AWS IAM with other services, not will pay the IAM; these are temporary security credentials.
How to Access AWS IAM
You can work with AWS Identity Access Management with 3-ways, and these ways are as following;
- AWS Management Console
- AWS Command Line Interface (CLI) IAM
- AWS Software Development Kits (SDK’s) IAM
1:AWS Management Console
The AWS console is a browser-based interface to manage AWS resources & services, IAM service, AWS S3, AWS EC2, Lightsail, and many other services.
2:AWS Command Line Interface (CLI) IAM
You can use the CLI to run commands in your system. Using the command line is faster and easier than using a console. Command-line tools are also helpful in creating scripts that perform AWS tasks and other services.
3:AWS Software Development Kits (SDK’s) IAM
AWS SDKs (software development kits) consisting of libraries and sample code for different programming languages (Python, Java, .NET, Ruby, iOS & Android platforms, etc.). The SDKs provide an easy way to create programmatic access to IAM and AWS.
AWS IAM Security Terminology
- Root Account
- IAM User
- IAM Roles
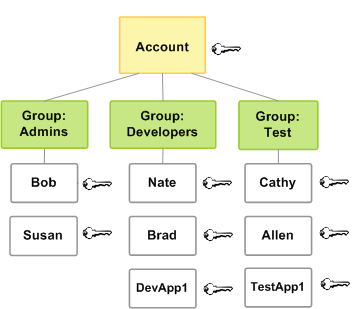
- IAM Groups
- Access Keys
- IAM Policies
- Security Group
- Billing Alert
- AWS IAM Budget
1:Root Account
When you first create an AWS console account with complete access to all AWS services, this account is known as the AWS root account.
2:AWS IAM User
IAM Users are not separate AWS accounts; these users are of the IAM service of your AWS console account. You have your AWS root account, email, and password to get into the AWS Console.
You can use this service for yourself and for any other function to which you need to give access. It can include people & applications, etc. Each user has their password and their access keys.
The best practices of AWS IAM, per Amazon, are creating an IAM user for themselves, allowing the admin, and using it for all their arrangements, including creating other users. You should also lock down both the root user and any administrative users using 2FA, which now supports authentication apps such as Google Authenticator.
3:AWS IAM Roles
IAM Rules is an organization that has permissions assigned to users but does not have credentials because you are handling this role with an existing user. They are suitable when different users play a given role at different times.
4:AWS IAM Groups
A collection of users. Groups allow you to define permissions for all the users within them.
5:Access Keys & Secret Keys
The access key and Secret Key are long-term credentials for an AWS IAM user or the AWS account root user. You can use these keys to sign programmatic requests through the AWS CLI.
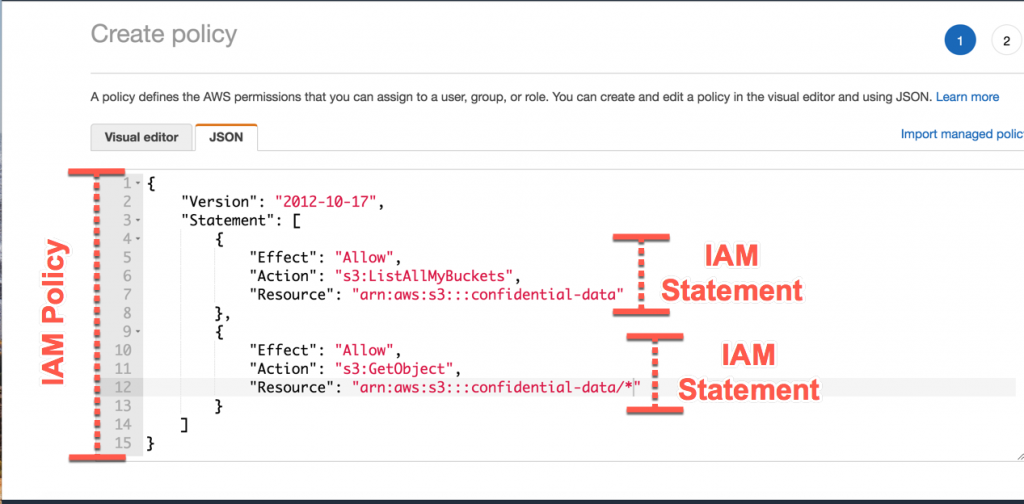
6:AWS IAM Policies
IAM policies define permissions through the policy for action regardless of the method you want to use to operate. IAM policies are stored in the JSON documents.
Policy types
- Identity-based policies are JSON policies and also all IAM policies have been stored in the JSON format that controls what actions an identity (users, groups of users, and roles) want to perform, on which resources, on which services, and under what conditions.
- Resource-based policies are JSON policy documents that you attach to services such as an Amazon S3 bucket & EC2 etc. IAM policies apply the specified principles to perform specific actions on that resource and define what conditions this applies to.
- Access Control Lists (ACLs) are AWS service policies that allow you to control which rules in another account can access AWS resources/services. We cannot use ACL to control all access to the principal in a single account. Although ACLs are the only policy type that does not use the JSON policy format, ACLs are like resource-based policies. Examples are AWS S3 and VPC services that support ACLs.
7:AWS Security Group
A security group works as a virtual firewall to control inbound and outbound traffic through multiple protocols.
Note. They’re firewall rules.
You define the protocols, ports, and what source IP can access those ports. And there are some presets for common ports, e.g., HTTP, HTTPS, SSH, ALL ICMP, TCP, etc. One incredible service is that you can share the rules across different ways without recreating them, almost like policies, except for network traffic.

8:Billing Alert/Alarm Alert Notification
- This data includes the estimated charges for every service in AWS that you use, and also has additional charges but the additional charges are only for some services.
- The alarm triggers when your account billing exceeds the limit you have specified.
9:AWS IAM Billing Access
IAM is a popular service of your AWS account offered at no additional charge. You will be paid only for the use of other AWS services by your AWS IAM users.
IAM Summary
Ok, here they are again in the quick form.
In this article, we have considered the concept of IAM service and all its features. This is one of the essential services that we must properly set up for any application for any organization, and other activities are initiated. Here are some of the best tips from Amazon Web Services when designing an IAM framework. As already mentioned in the article, there are two ways to access multiple services on AWS, either through usernames and passwords or using access and secret keys. You should keep an active eye on your account and monitor your AWS account activities.
It is best to enable 2FA security on an admin-level account. Access keys are SSH keys. They are how you verify your infrastructure. IAM policies are a set of permissions that we may assign to users or groups. Security groups are basically firewall rules.
I hope this helps someone increase AWS knowledge faster than going through the documentation themselves.
Also Read: AWS Lightsail — Pros, Cons & Best Resources to Learn




